How does email DKIM work?
DKIM can be confusing at first, but it's one of the best ways to secure your email communications.
2023-06-19 • Updated: 2024-02-05
DKIM can be confusing at first, but it’s one of the best ways to secure your email communications. Here is an outline of the authentication method and some answers to questions you might have.
DKIM (DomainKeys Identified Mail) is a method for email authentication that allows the recipient to verify that an email message was actually sent by the domain it claims to be from, and that the message has not been altered in transit.
Here’s how DKIM works:
- The sending mail server generates a digital signature for the email message. This signature is based on the contents of the message header and body, as well as a private key that is unique to the sending domain.
- The signature is added to the message header as a DKIM-Signature field.
- When the email message is received by the recipient’s mail server, the server retrieves the public key for the sending domain from DNS (Domain Name System) records.
- The server uses the public key to decrypt the digital signature in the DKIM-Signature field and verify that the signature is valid. If the signature is not valid or cannot be verified, the email may be rejected or marked as spam.
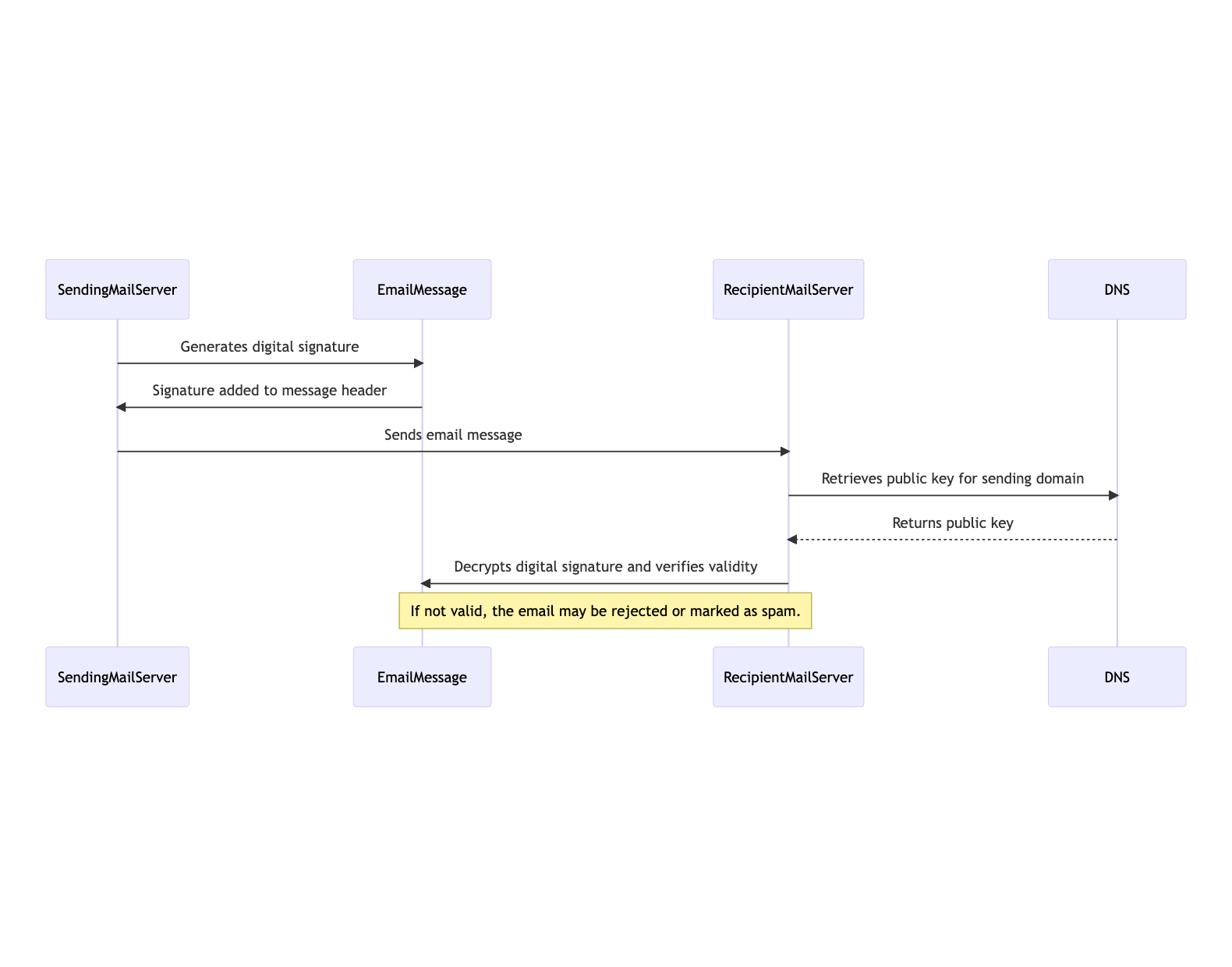
By using DKIM, email receivers can trust that the email was indeed sent by the domain it claims to be from, and that the message has not been tampered with in transit. This helps to prevent email spoofing and phishing attacks, which can be used to trick users into divulging sensitive information or downloading malware.
How does the server retrieve the public key?
When an email message is received, the receiving mail server can retrieve the public key for the sending domain from DNS (Domain Name System) records.
The public key is published in a DNS TXT record under a specific subdomain, typically named “default._domainkey”. The subdomain is created by the domain owner and contains a public key in the form of a long string of characters.
For example, if the sender’s domain is “example.com”, the receiving mail server can query the DNS for the TXT record of “default._domainkey.example.com”. The TXT record contains the public key that the receiving mail server needs to verify the signature on the email message.
Once the receiving mail server has retrieved the public key from the DNS record, it can use it to decrypt the digital signature in the DKIM-Signature field and verify the authenticity of the email message.
What if default._domainkey is not the user?
If the “default._domainkey” subdomain does not exist or is not set up for the sending domain, DKIM verification will fail, and the email message may be rejected or marked as spam.
In order for DKIM to work correctly, the domain owner must publish the DKIM public key in a DNS TXT record under the “default._domainkey” subdomain. The public key must be generated by the domain owner and should be kept secret, as it is used to generate the digital signatures for all outgoing email messages.
If the domain owner has not set up DKIM, or if the DKIM configuration is incorrect, DKIM verification will fail, and the email may be treated as suspicious or fraudulent. In such cases, the recipient mail server may apply additional anti-spam or anti-phishing measures, or the email may be rejected outright.
Why is it called default._domainkey?
The subdomain “default._domainkey” is the default name used for the DKIM public key record in DNS. This naming convention is specified in the original DKIM standard (RFC 4871).
The subdomain name is constructed using the literal string “default._domainkey” followed by the domain name of the sender. The subdomain name is used to identify the DKIM public key record in DNS and allows for multiple DKIM keys to be published for different purposes or subdomains.
For example, if a domain owner wants to use different DKIM keys for different email services, they can publish separate keys under different subdomains. They might use “mail._domainkey” for their email service and “news._domainkey” for their newsletter service, for instance.
In summary, the “default._domainkey” subdomain is the default naming convention for DKIM public key records in DNS, and it helps identify the public key for a specific domain name.
Suppose they use different DKIM keys. How does the mail server know what they are?
When a receiving mail server receives an email message, it looks up the DKIM public key for the sender’s domain in DNS by querying the “default._domainkey” subdomain, as we discussed earlier.
However, it’s possible for a domain owner to use different DKIM keys for different subdomains or email services. In that case, the domain owner would need to create separate DKIM public key records for each subdomain or email service, and publish them in DNS under their corresponding subdomain.
For example, if a domain owner has two subdomains: “mail.example.com” and “news.example.com”, they could publish two separate DKIM public key records in DNS under the “mail._domainkey.example.com” and “news._domainkey.example.com” subdomains respectively.
When an email message is received, the receiving mail server can query the appropriate DKIM public key record in DNS based on the domain or subdomain from which the message was sent. By using the correct DKIM public key, the receiving mail server can verify the digital signature and determine whether the message is authentic and has not been tampered with in transit.
In summary, if a domain owner uses different DKIM keys for different subdomains or email services, they must publish separate DKIM public key records in DNS for each one. The receiving mail server can then look up the appropriate DKIM key in DNS based on the domain or subdomain from which the email was sent.
Suppose the public key is incorrect. Can you find the domain it’s connected to?
If the public key in a DKIM signature is incorrect or invalid, it may not be possible to determine the domain it is associated with directly from the signature. However, DKIM signatures include information about the domain used to generate the signature, so it may be possible to identify the associated domain by examining the DKIM signature header.
The “d=” tag in the DKIM signature header specifies the signing domain that is responsible for generating the DKIM signature. The receiving mail server can use this information to query DNS and retrieve the DKIM public key for the associated domain.
If the DKIM public key retrieved from DNS does not match the public key in the DKIM signature, the email may be treated as suspicious or fraudulent, and additional anti-spam or anti-phishing measures may be applied.
In summary, if the public key in a DKIM signature is incorrect, it may be possible to identify the associated domain by examining the DKIM signature header and retrieving the DKIM public key from DNS. However, this may not always be possible, and DKIM verification may fail if the public key is invalid or cannot be retrieved.
How do you generate a private key?
To generate a private key for DKIM, you can use a cryptographic key generation tool, such as OpenSSL. Here are the basic steps to generate a private key:
- Install OpenSSL on your system, if it is not already installed.
- Open a command prompt or terminal window.
- Type the following command to generate a private key:
openssl genrsa -out private.key 2048
This command generates a 2048-bit RSA private key and saves it to a file named “private.key” in the current directory.
4. Securely store the private key. You should keep the private key in a safe place and protect it from unauthorized access. It’s also a good idea to create a backup copy of the private key and store it in a separate location.
Once you have generated the private key, you can use it to generate the DKIM signature for your outgoing email messages. The public key corresponding to the private key should be published in a DNS TXT record under the “default._domainkey” subdomain of the sending domain, as we discussed earlier, so that recipients can verify the authenticity of the email messages.
Where is the private key stored?
The private key generated for DKIM is a sensitive piece of information that should be stored securely to prevent unauthorized access. Typically, the private key is stored in a file on the server that is responsible for sending email on behalf of the domain. The location of the private key file can vary depending on the email server software being used, but it is usually located in a specific directory, such as “/etc/opendkim/keys” for OpenDKIM.
It is important to ensure that the private key file is only accessible by the email server software and authorized administrators. To achieve this, file permissions should be set so that only the owner of the file (i.e., the email server user) has read and write access, and other users have no access to the file.
It’s also a good idea to create a backup copy of the private key and store it in a secure location, such as an encrypted USB drive or a password-protected cloud storage service. This ensures that you have a copy of the private key in case the original file is lost or becomes corrupted.
How do you generate a public key?
To generate a public key for DKIM, you need to use the private key that you generated earlier. Here are the basic steps to generate a public key:
1. Open a command prompt or terminal window.
2. Type the following command to generate the public key:
openssl rsa -in private.key -outform PEM -pubout -out public.key
This command reads the private key file “private.key”, and generates a corresponding public key in PEM format, which is saved to a file named “public.key” in the current directory.
3. Securely store the public key. The public key should be published in a DNS TXT record under the “default._domainkey” subdomain of the sending domain, as we discussed earlier. You should also keep a backup copy of the public key in a safe place, in case it needs to be re-published or updated.
Once you have generated the public key, you can publish it in DNS, and use it to generate DKIM signatures for your outgoing email messages. The private key corresponding to the public key should be kept securely on the server that is responsible for sending email on behalf of the domain.
DKIM plays a crucial role in email authentication, providing a mechanism to verify the authenticity and integrity of email messages. By understanding how DKIM works and following the key generation process, domain owners can implement robust email authentication practices, reducing the risk of email fraud and impersonation.
Hopefully, this has demystified DKIM and answer some questions you make have related to email delivery.
Keep Reading
We think you may like these

WP Scanner Chrome extension
WP Scanner is a Chrome extension that checks any WordPress site you visit for technical and SEO issues


